In the realm of software security, this essay introduces the concepts of vulnerability assessment and exploiting.
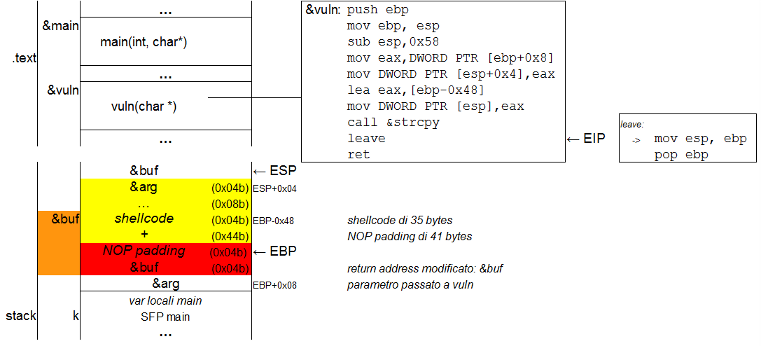
After that, it does a deep dive into the problem of stack based buffer overflows, assuming no preliminary knowledge about the topic and providing minimal code examples in C.
Discussed topics:
- payload preparation (shellcode)
- memory layout of a program
- function calls and how they use the stack
- the "stack smashing" exploiting technique
- countermeasures (ASLR, ProPolice, NX stack) introduced to mitigate the problem
A complete example of remote code execution against a vulnerable program is ultimately analyzed.
Source code, full text and slides (in Italian) are available for download:
full text slides slides (for printing) source code archive